Now more than ever, only those who know their weaknesses can effectively protect themselves from attacks.
A particularly alarming trend is the dramatic increase in Common Vulnerabilities and Exposures (CVEs), making Vulnerability Management (VM) a monumental task for enterprises.
The number of security vulnerabilities continues to rise
The most recent Microsoft Vulnerabilities Report finds an unprecedented level of vulnerabilities in Microsoft systems. The tenth edition of the report documents a total of 1,292 security vulnerabilities, breaking all previous records. This is even more concerning given the fact that Microsoft remains the No. 1 supplier of software for businesses.
For the third year in a row, the biggest security risk are excessive user authorizations. And as cloud solutions become more mainstream, it is also worth noting that vulnerabilities in Azure and Dynamics 365 have increased by 159%, from 44 in 2021 to 114 in 2022.
The challenge of Vulnerability Management

The situation has become particularly acute in the area of API security, with more interfaces exposing more sensitive data and business logic than ever before, dramatically exacerbating the vulnerability situation.
Every vulnerability in a software or hardware product is a potential gateway for attackers. And with an increasing volume of potential security vulnerabilities, it is becoming more and more challenging to identify and patch them effectively. This more than ever also illustrates the need for advanced approaches such as Risk-Based Vulnerability Management, which goes beyond simply identifying vulnerabilities. It prioritizes the remediation of those vulnerabilities that pose the greatest risk and allows for a better understanding of the associated business risks.
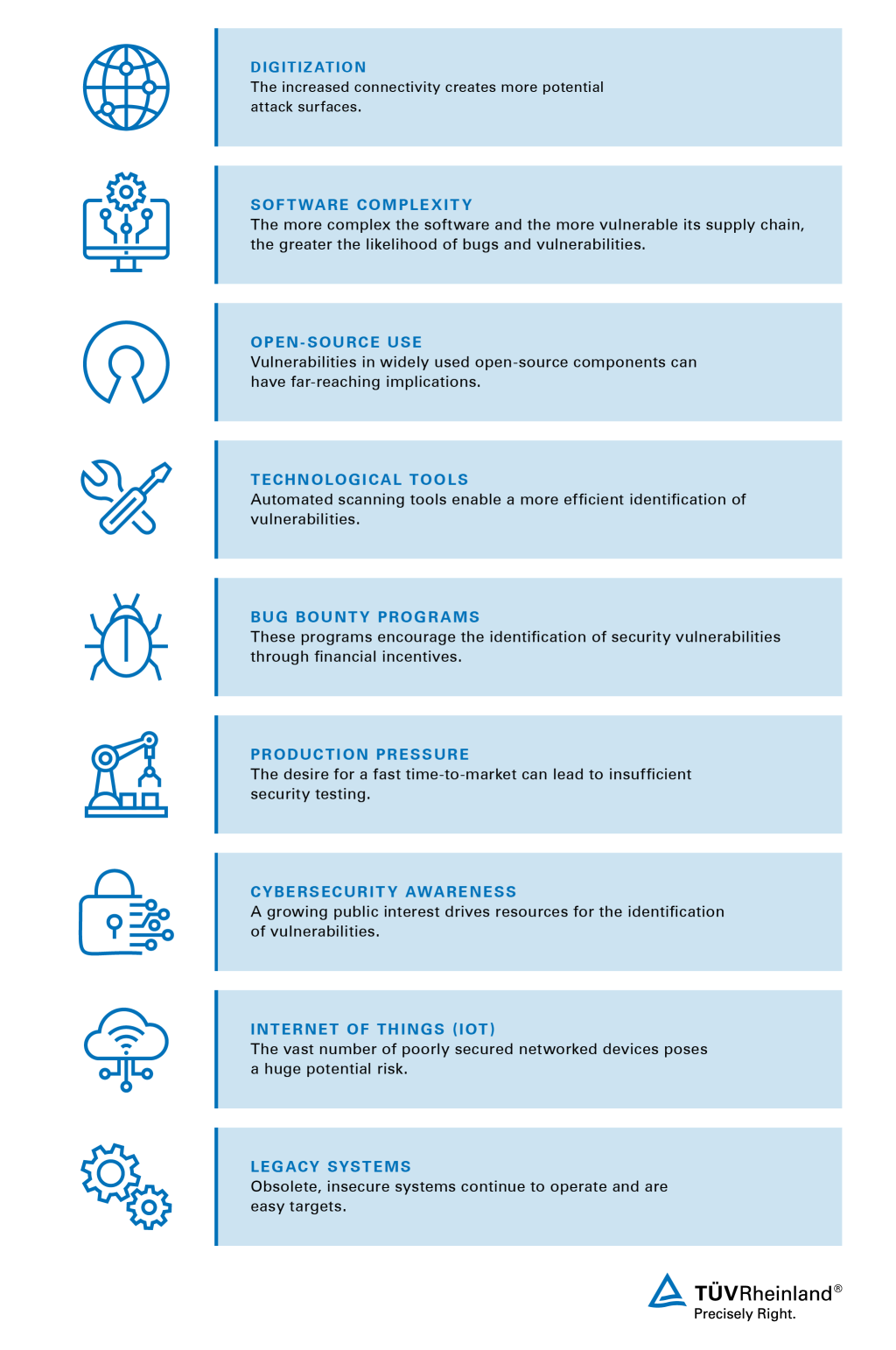
Why security gaps are increasing
Update systems and minimize vulnerabilities
Given the growing number and complexity of vulnerabilities, it is imperative for organizations to continuously update their security measures. Risk-Based Vulnerability Management and a deep understanding of the threat landscape are critical tools for operating effectively in this dynamic environment.
After all, only those who know their weaknesses can protect themselves effectively. Therefore, prioritizing and patching the highest risk vulnerabilities must remain the focus of any modern cybersecurity approach also in 2024.
Leran more about our cybersecurity services
When it comes to your cybersecurity, there is no one-size-fits-all solution. That's why we offer you a flexible range of services – tailored to your individual needs and requirements.
Do you want to close your security gaps? We're happy to help!






-cybersecurity-services-1_core_4_3.jpg)