Identity Access Governance Consulting

The New Digital Environment Requires Future-Proof IAG Solutions
The implementation of new services, remote working and the hybrid of on-premise solutions and cloud services provide a more efficient way of working in the digital environment. Connecting the IT world with the Internet of Things (IoT) and industrial operational technology (OT) has been rapidly increasing the number of access points that need to be managed. This creates new challenges and risks, as an incorrect or carelessly implemented access management can be a threat to your company's cybersecurity.
With our Identity Access Governance (IAG) Consulting, we support you in the secure management of roles, accesses and identities. In addition to a comprehensive analysis of your status quo, we provide you with expert advice on potential approaches and solutions for an effective, flexible IAG.
You can trust in our many years of experience in the field of cybersecurity. Thanks to our expertise and our integrated approach, we support you with great competence and with an optimal return on investment.
Integrated Approach for a Successful User Management
Your organization operates across a sophisticated and unique network of people and IT systems, resulting in cybersecurity requirements that are specific to your particular needs. Future-proof IAG solutions must therefore be designed to flexibly address new and evolving security requirements and threats.
Implement a sustainable, flexible solution for access management and identity management for your organization. With our detailed analysis of your current state and the combination of examining the risks and your protection needs, we create a customized solution tailored to your needs where we assist you with the development of a long-term identity access governance strategy or even partial Best of Breed solutions. From planning to implementation – we will be at your side as your competent, trusted partner.
Customized Integrated IAG Solutions
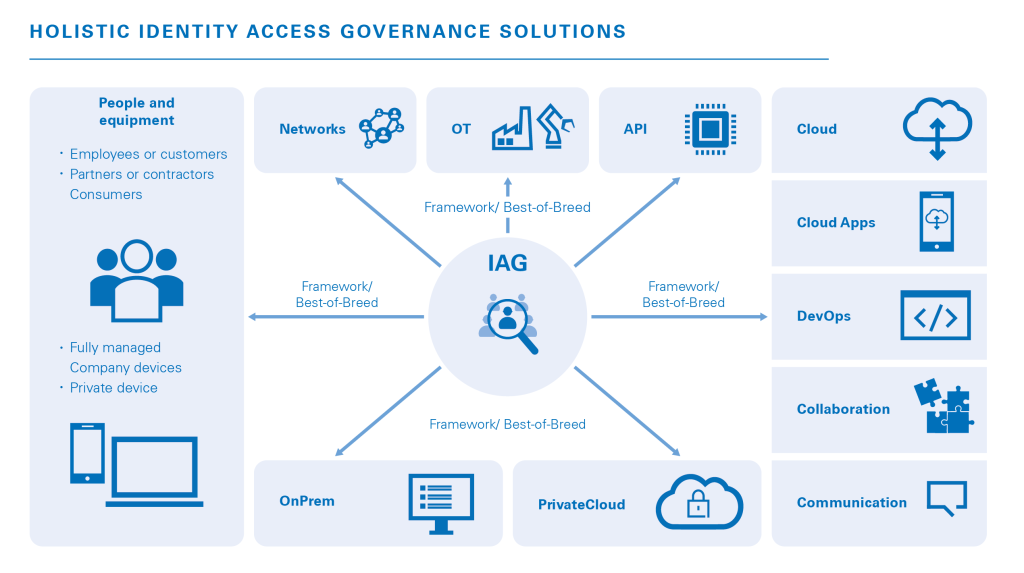
Each of our tried and trusted consulting steps is tailored to your needs to help you achieve an optimal, customized result. For this purpose, our experts utilize a modular structure that breaks down the entire project into single steps. In general, these individual steps can be implemented independent of each other, but they can also be combined.
Specifically, we look in detail at:
- People and devices
- Networks
- Operational Technology (OT)
- Application Programming Interfaces (APIs)
- (Private) clouds and cloud apps or on-premise-solutions
- DevOps
- Collaborations
- Communication channels
Four Levels of IAG Consulting
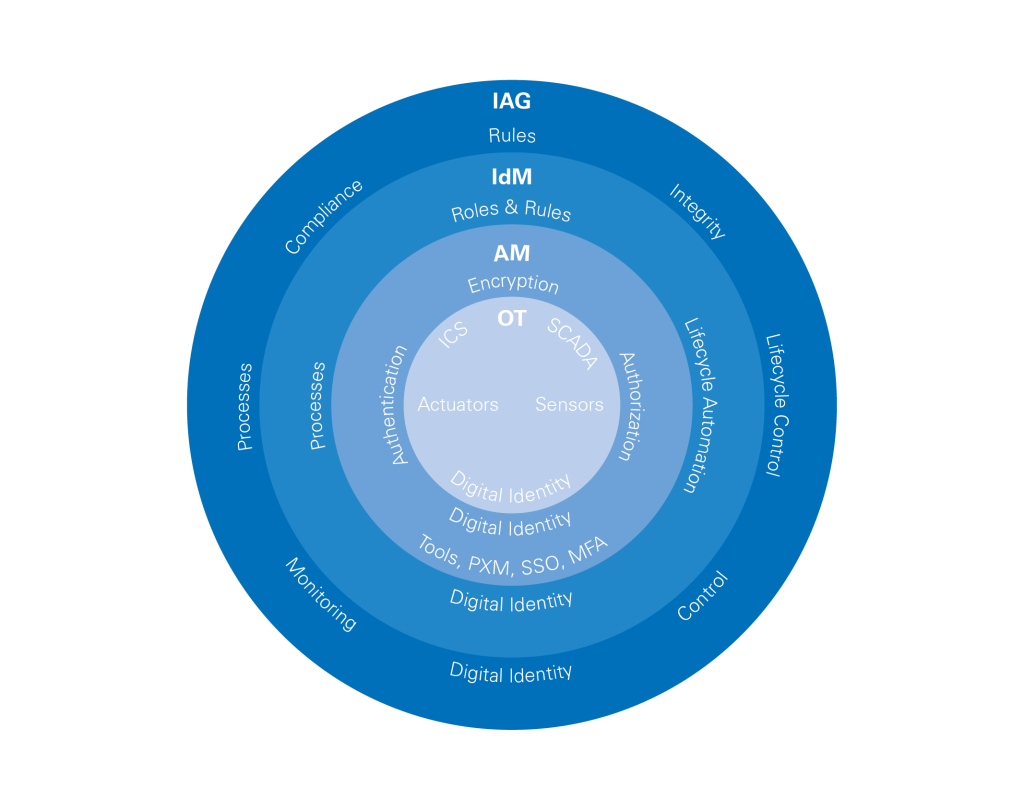
We provide support for both a holistic realignment of the system and for the adaptation of individual aspects. Our consulting services are divided into four levels with varying degrees of detail, covering strategic consulting (IAG) as well as short-term recommendations for action (Identity Management (IdM) and Access Management (AM)). In addition, there are Operational Technologies (OT) and Information Technologies (IT), which are the true components of the system.
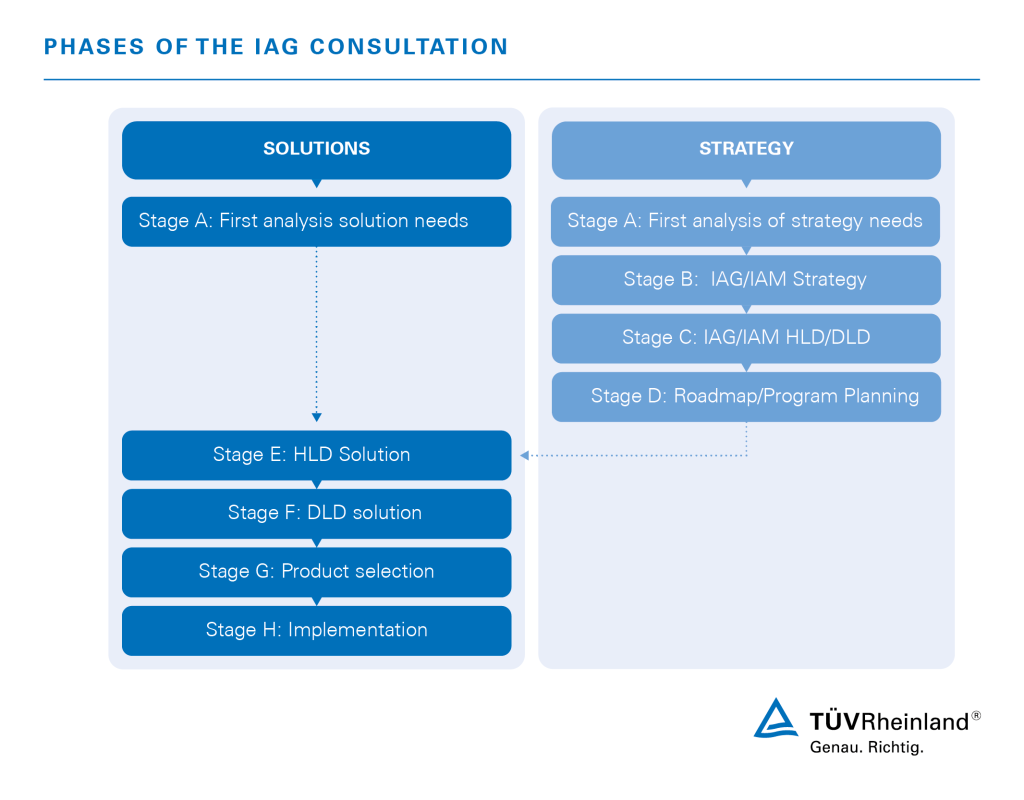
Our Access Governance Consulting Procedure
Our IAG consulting consists of modular solutions that we develop together with you in different phases. Learn more about the different phases in our detailed graphic .
We Offer you Experienced and Competent Advice
Trust our expertise when developing your Identity Access Governance solution. With our many years of experience in cybersecurity and IT, our experts can develop and implement your access governance strategy in a timely and efficient manner. Thanks to our global network, we are always close to you, ensuring short communication paths and international know-how.
You want to implement a resilient IAG strategy? Request your customized quotation!
FAQ: Answers to Your Questions about TUV Rheinland’s IAG Solution
Are you interested in Identity Access Governance, but still have questions? Our experts have summarized the answers to frequently asked questions for you. Don't hesitate to contact us if your question has not been answered.
Contact your IAG expert!



-cybersecurity-services-1_core_4_3.jpg)
